
This episode is a short discussion about how to make memory useful. If you want more – ping us via our Twitter account: @CQUREAcademy. For this episode, we assume that you have made your dump and that you will use it for today’s analysis. We will present to you an interesting technique for grabbing the information from the memory:
Passwords in a dump file
First of all, you will need a second Windows 10 virtual machine.
Go to remote desktop settings and enable remote desktop. You will need one more thing from this machine and that is your PC name seen on the bottom after you turn on remote desktop option.
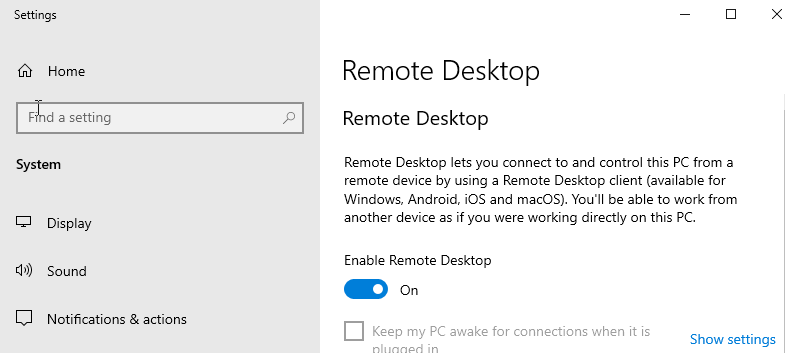
Once that is done, we can move on to the second machine. We will be using mimikatz to extract the password from the machine to which we are connecting.
To initiate the connection, open Remote Desktop Connection. You will be asked to fill in the PC name to which you are connecting and credentials to an account.
Once the connection has been established perform the dump of the lsass.exe process on the machine from which you are connecting (you can use Task Manager or procdump.exe from Sysinternals Tools, we suggest: procdump.exe – ma). In Mimikatz connect directly to the dump – see the screen below:


Then directly extract credentials from the memory dump in order to get some useful and juicy data:
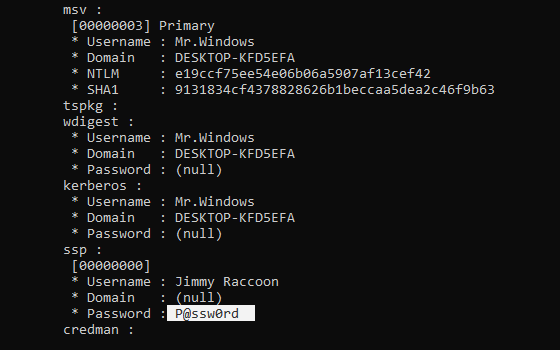
What is great about this approach is that it prevents running different 3rd party software on servers. The dump does not hurt anybody and later on, you are capable to analyze it locally.
We can see that the password of the account to which we connected is visible in plain text in lsass process on the machine which initiated the connection.
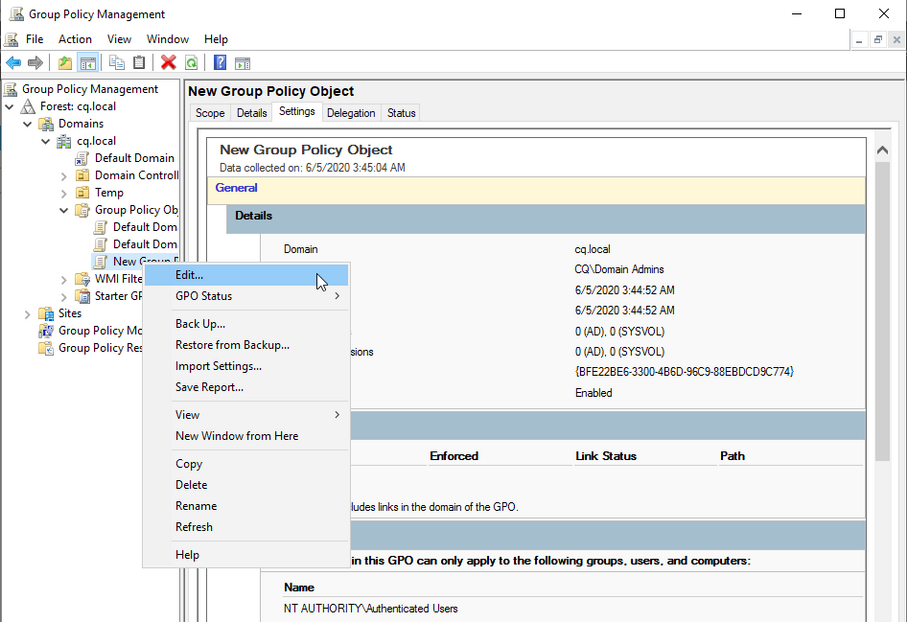
To prevent this, create a GPO (Group Policy Object) which will force clients to connect to remote systems using Restricted Admin mode. To do so open Group Policy management and navigate to group policy objects and create a new GPO. Then right-click on the newly created Group Policy and select edit.
Then navigate to Policies – Administrative Templates – System – Credentials Delegation and set Restrict delegation of credentials to remote servers to enabled.
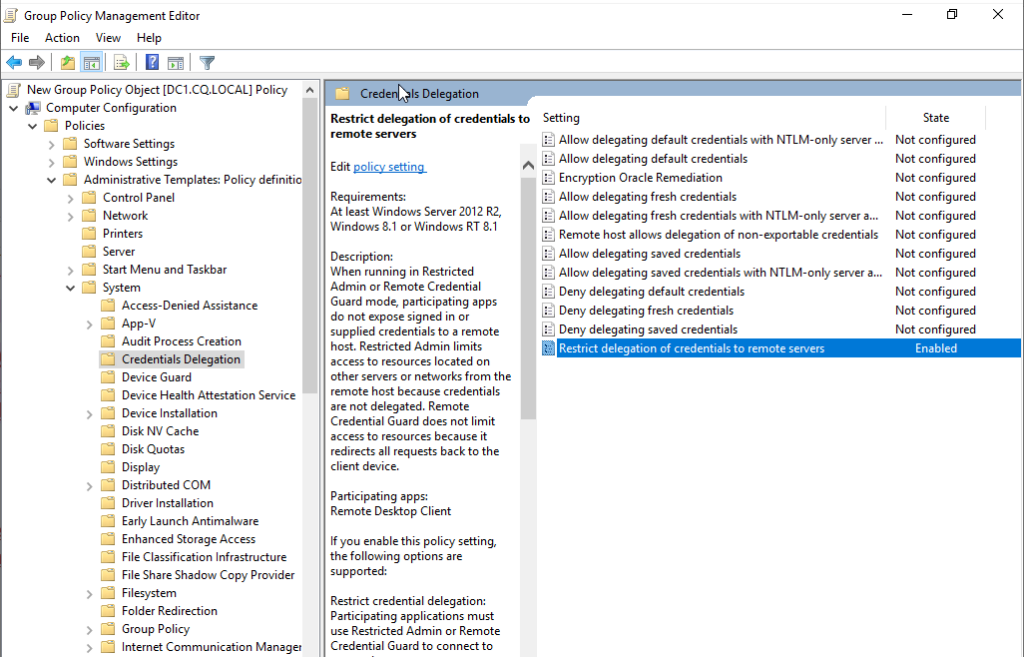
Furthermore, the DisableRestrictedAdminOutboundCreds registry key should be created with the value 1 to disallow network authentication from inside the system that the admin has performed the RDP. The absence of this key means that the Admin outbound credentials are enabled. This policy should be enforced across the domain to make sure all RDP sessions are using Restricted Admin.
Another option is using the Windows Credential guard or running lsass as a protected process.
We hope that after this quick memory analysis walkthrough you now see it can be truly practical. Especially when you are searching for some traces or troubleshooting chosen situation. We hope you can’t wait for the next, last episode! We can’t!
Stay safe!
CQURE Experts



Do you want to receive the geekiest cybersecurity solutions, tools, and tricks, straight to your inbox?
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.