
Identity Protection is a security feature in Azure Active Directory that helps to prevent, detect, and remediate identity risk in an organization. Using multiple detections, it monitors every login for identity compromise, sorting sign-ins into three categories of risk: low, medium, and high. These risk ratings can be used to create automated user risk policies […]
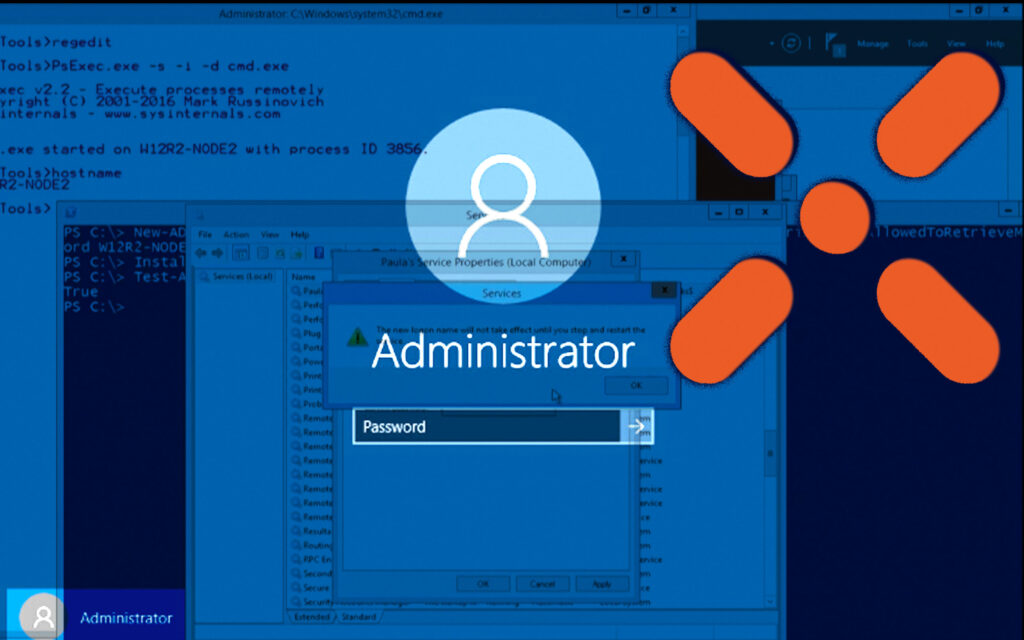
Learn how to extract passwords from the service accounts and how to implement gMSA (group Managed Service Accounts) in order to manage the identity of services correctly.
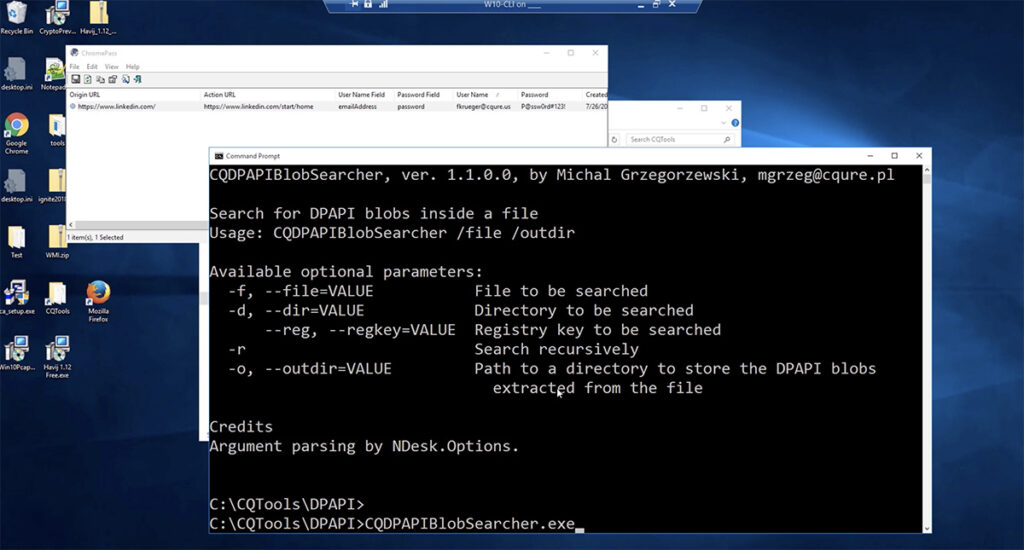
What is DPAPI? Data Protection Application Programming Interface (DPAPI) is used in many Windows applications and subsystems. What is its purpose? For example: Credentials of Microsoft Outlook accounts stored in the registry; Credentials and encrypted cookies stored by Google Chrome; Credentials stored by IE in the registry under HKCU\Software\Microsoft\Internet Explorer; WiFi passwords saved in XML […]
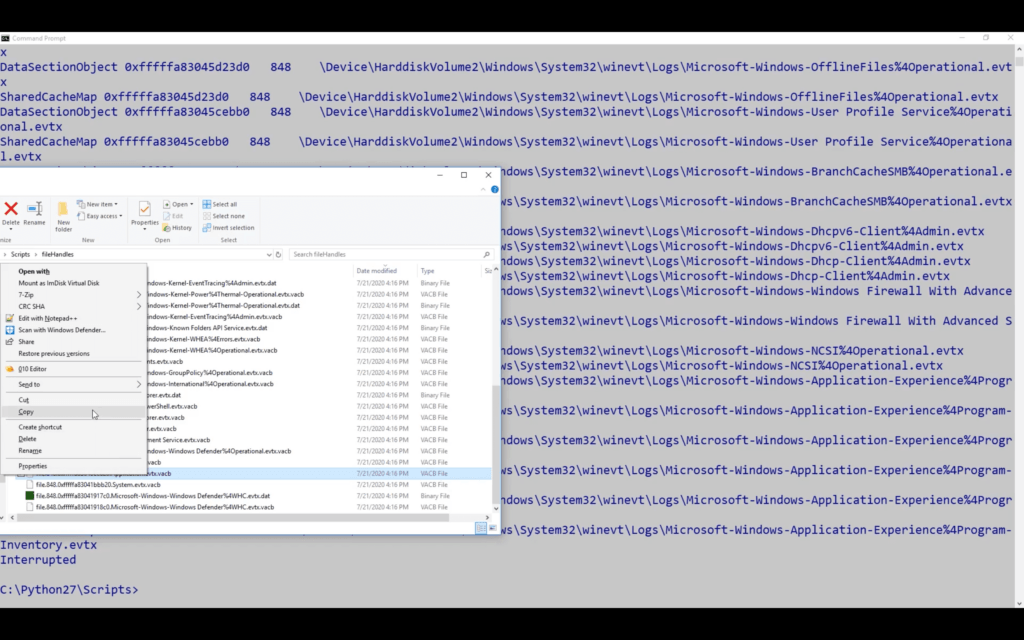
Find out: how to recover corrupted EVTX log files recover log files directly from a memory dump Watch the full video for more details and examples. Tools for EVTX file recovery Our experts developed this particular tool because there are so few options available online for fixing EVTX files. Try our CQEVTXRecovery tool. It is […]
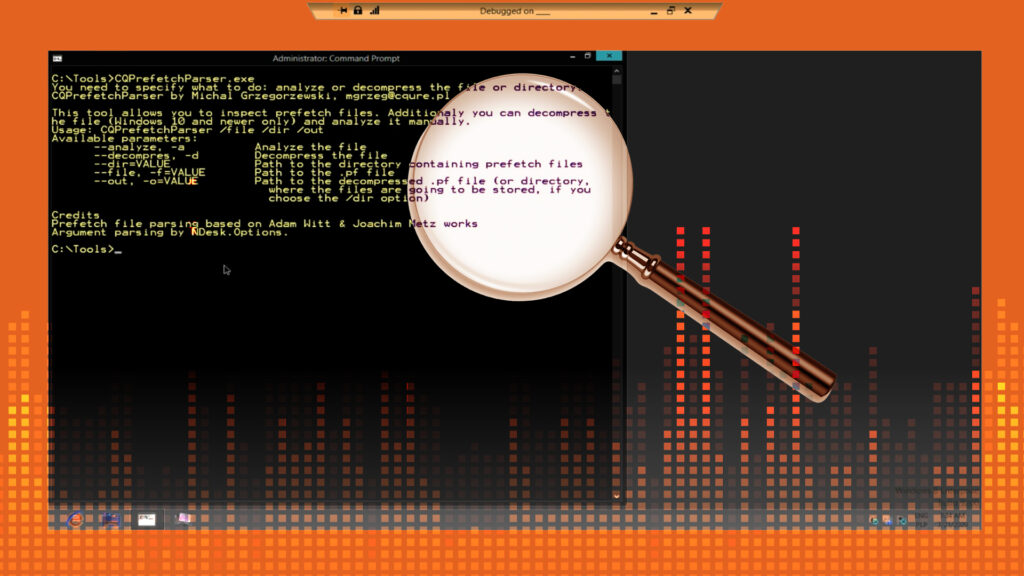
Prefetch files offer a digital snapshot of events inside your Windows operating system (OS). Because they are created when an executable program is run from a particular location for the very first time, forensic specialists can use these files to determine what was running and when. In the event of a cyber-attack, the timeline of […]
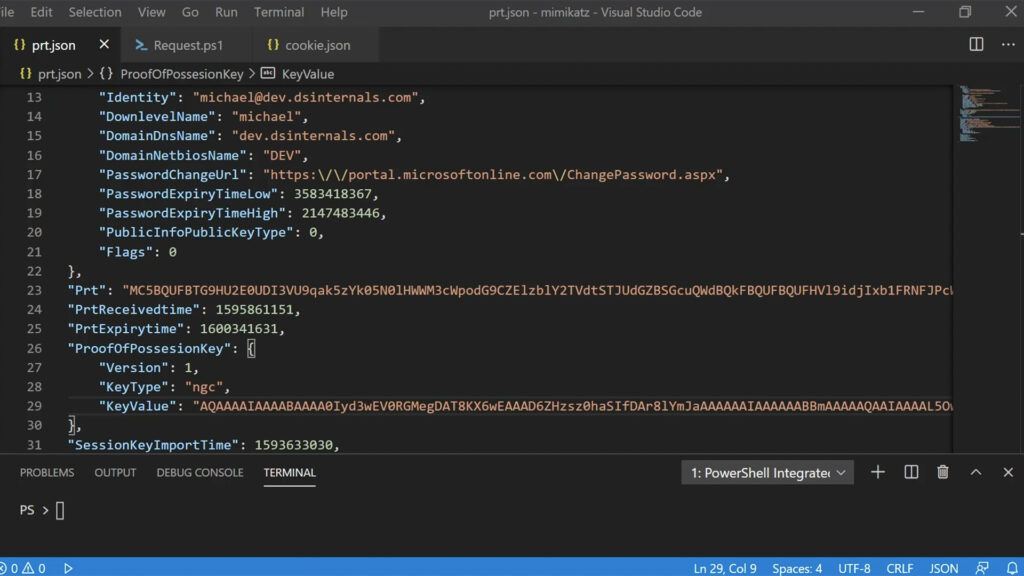
Discover what a Primary Refresh Token is and how cyber-criminals are exploiting it in two different ways to launch Azure Active Directory attacks.
Find out how Paula J, CQURE Academy CEO performs Man-in-the-middle attack, to know what to be aware of.

Find out how Paula J, CQURE Academy CEO performs Man-in-the-middle attack, to know what to be aware of.
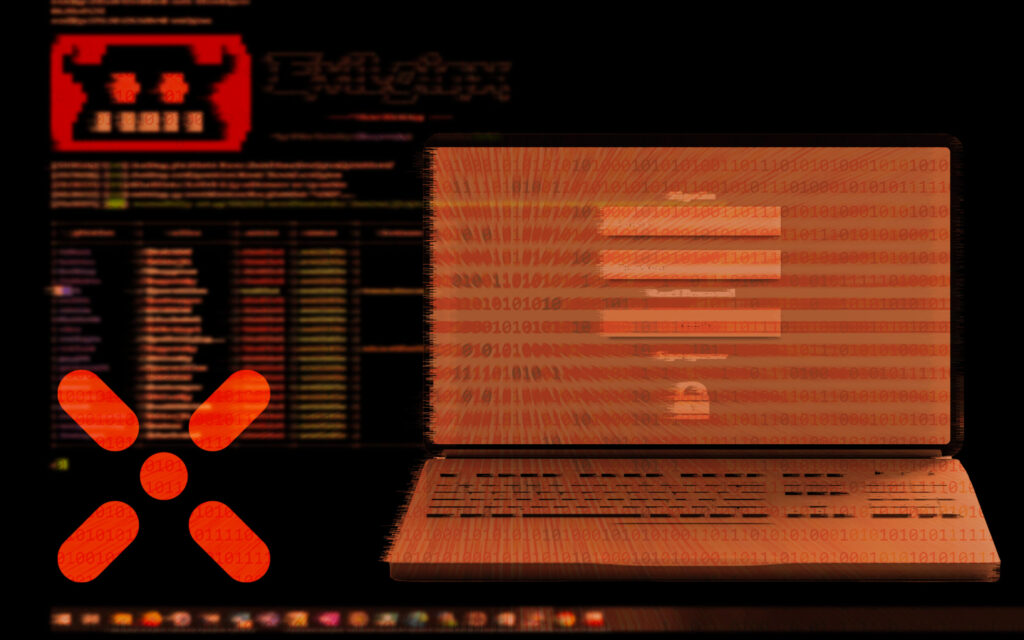
Paula Januszkiewicz demonstrates a social engineering attack in which Evilginx is deployed to phish Microsoft Teams login credentials.
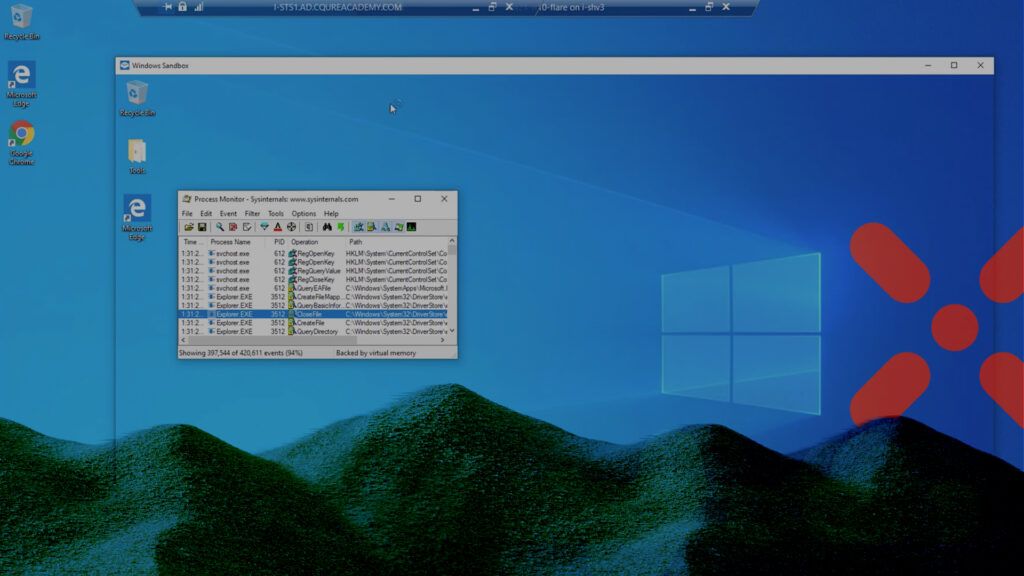
Windows Sandbox can protect your PC from malicious executables. Here’s how to install and configure it correctly from a security expert.












