
Thanks to the great work of the case attorney Simone Bertollini and CQURE’s team and our pretty amazing know-how this is the first hacking case in history that was WON by the defenders! “The CQURE Team identified serious flaws in the government’s investigation. They helped me do justice for Gasperini” – stated Simone Bertollini. Learn […]

In this article we are going look into the process authentication with ADFS. We will use “Fiddler” – free web debugging proxy tool to analyze network conversation between website to which user is authenticating and its web browser. This is a very useful tool for troubleshooting ADFS authentication problems and we will learn what the […]
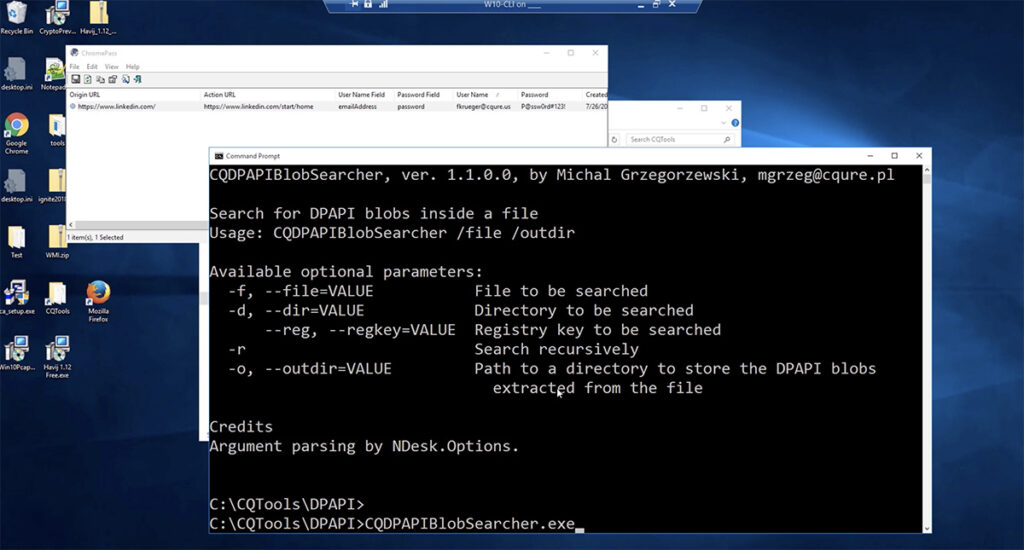
What is DPAPI? Data Protection Application Programming Interface (DPAPI) is used in many Windows applications and subsystems. What is its purpose? For example: Credentials of Microsoft Outlook accounts stored in the registry; Credentials and encrypted cookies stored by Google Chrome; Credentials stored by IE in the registry under HKCU\Software\Microsoft\Internet Explorer; WiFi passwords saved in XML […]
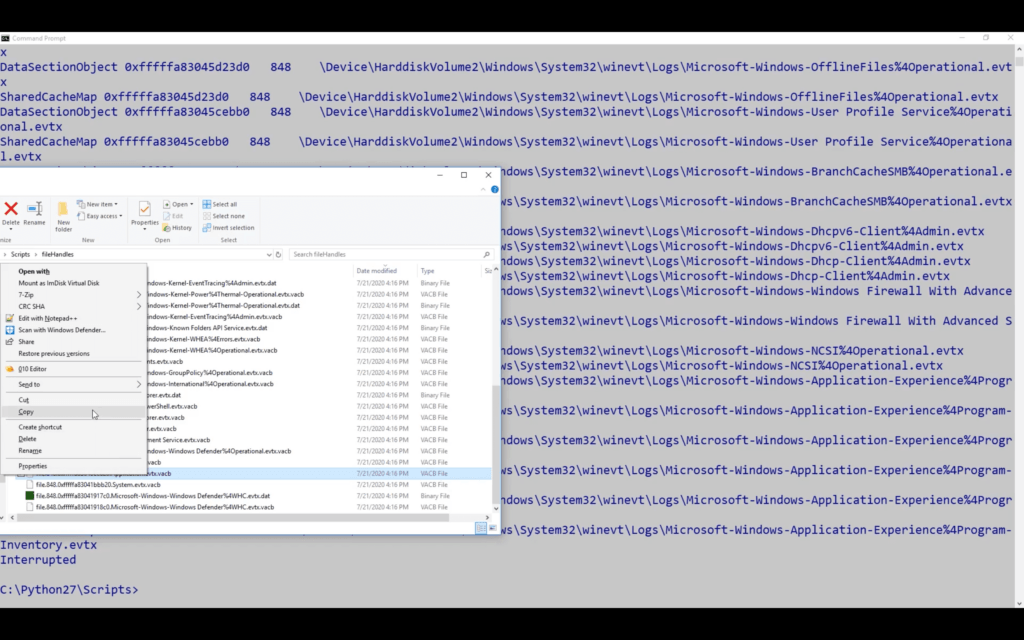
Find out: how to recover corrupted EVTX log files recover log files directly from a memory dump Watch the full video for more details and examples. Tools for EVTX file recovery Our experts developed this particular tool because there are so few options available online for fixing EVTX files. Try our CQEVTXRecovery tool. It is […]
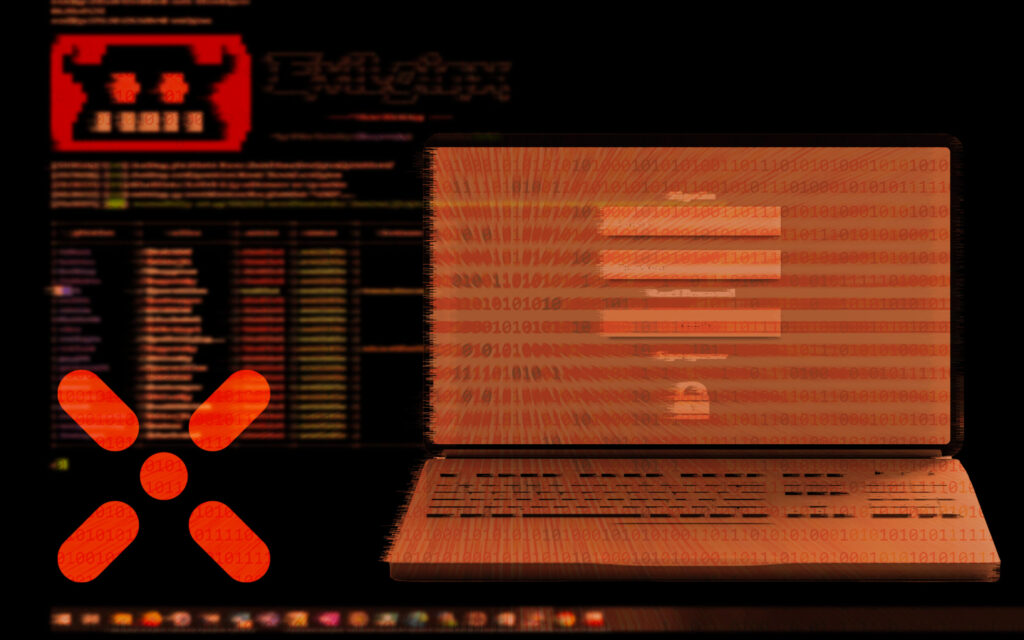
Paula Januszkiewicz demonstrates a social engineering attack in which Evilginx is deployed to phish Microsoft Teams login credentials.

Protecting your digital treasure trove means avoiding those Azure AD misconfigurations that attackers are waiting to exploit. Use CQURE’s guide to detect and remedy some of the most common AD misconfiguration mistakes.






