We are in an age where technology is becoming more and more advanced each day. Yet, in parallel, hackers and the cyber threats they launch have also become more sophisticated. It is now easier than ever to fall victim to cyberattacks.
What can the community of IT professionals and cybersecurity experts do to protect our companies and community?
To answer that question, take a deep dive into social engineering and learn:
Social engineering is one of the sophisticated tricks that cybercriminals use. It is a malicious hacking technique used to manipulate people into performing actions or divulging confidential information by using a variety of techniques, from exploiting human nature to impersonating someone in a position of authority.
There are 10 types of social engineering strategies: phishing, spear phishing, vishing, baiting, malware, email hacking and contact spamming, pretexting, quid pro quo, tailgating, and water holing.
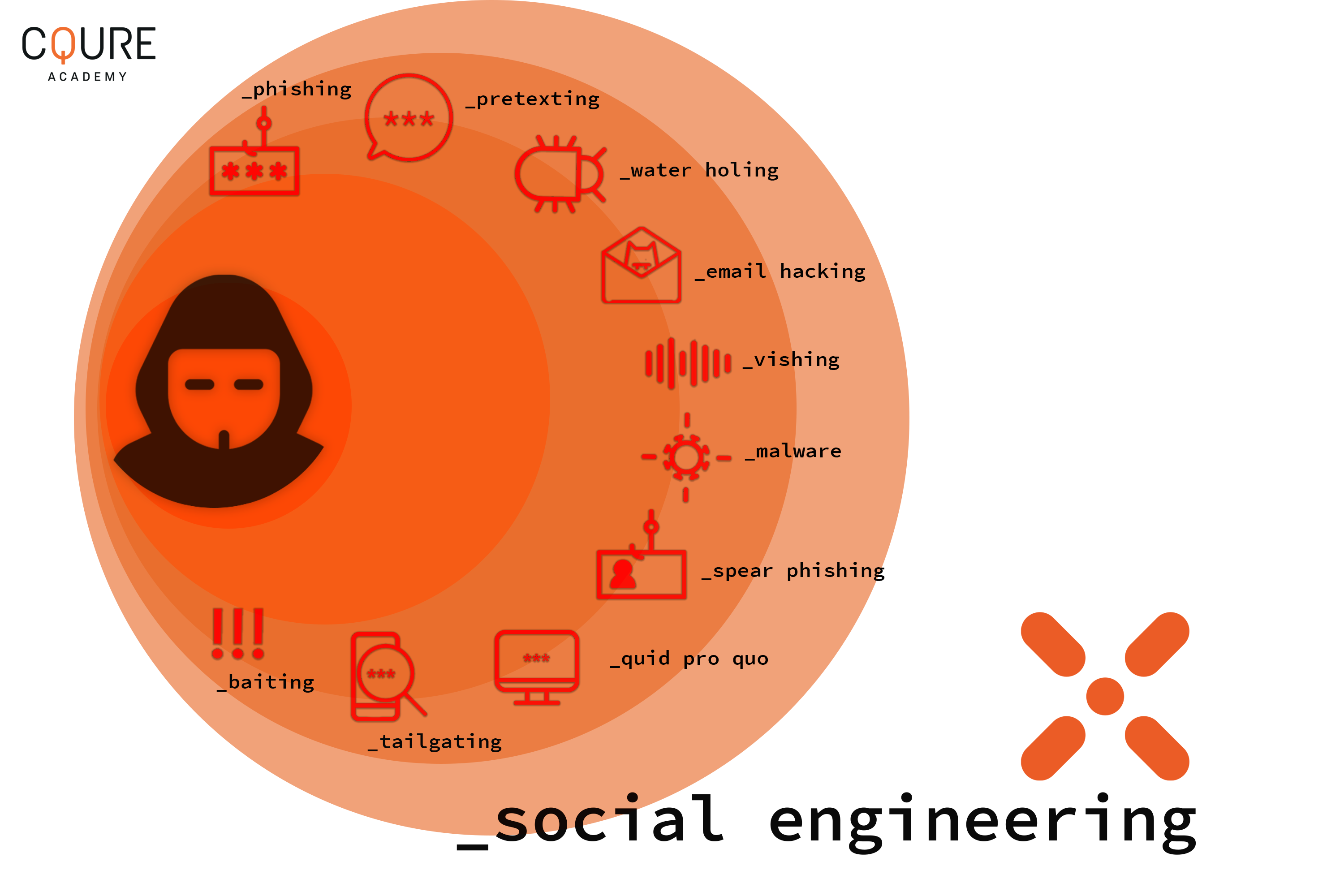
Here, we will focus on phishing and its close variants since it is one of the most popular forms of social engineering.
Phishing is one of the most common types of social engineering that can happen to virtually anyone. Hackers use this technique to trick you into giving up your private information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.
These tactics include deceptive emails that often direct users to enter details at a fake website that looks and feels almost identical to the legitimate one. Around 96% of phishing attacks happen by using bait via email, with text messages being another way for hackers to lure people to illegitimate sites intended to steal their information.
Other variants of phishing are spear-phishing and vishing. The former uses email to carry out targeted attacks against individuals or businesses while the latter gets its name from “voice phishing”. Vishing is one of the fastest-growing types of social engineering that usually employs Voice over Internet Protocol (VoIP) technology to impersonate a customer service agent from a major company.
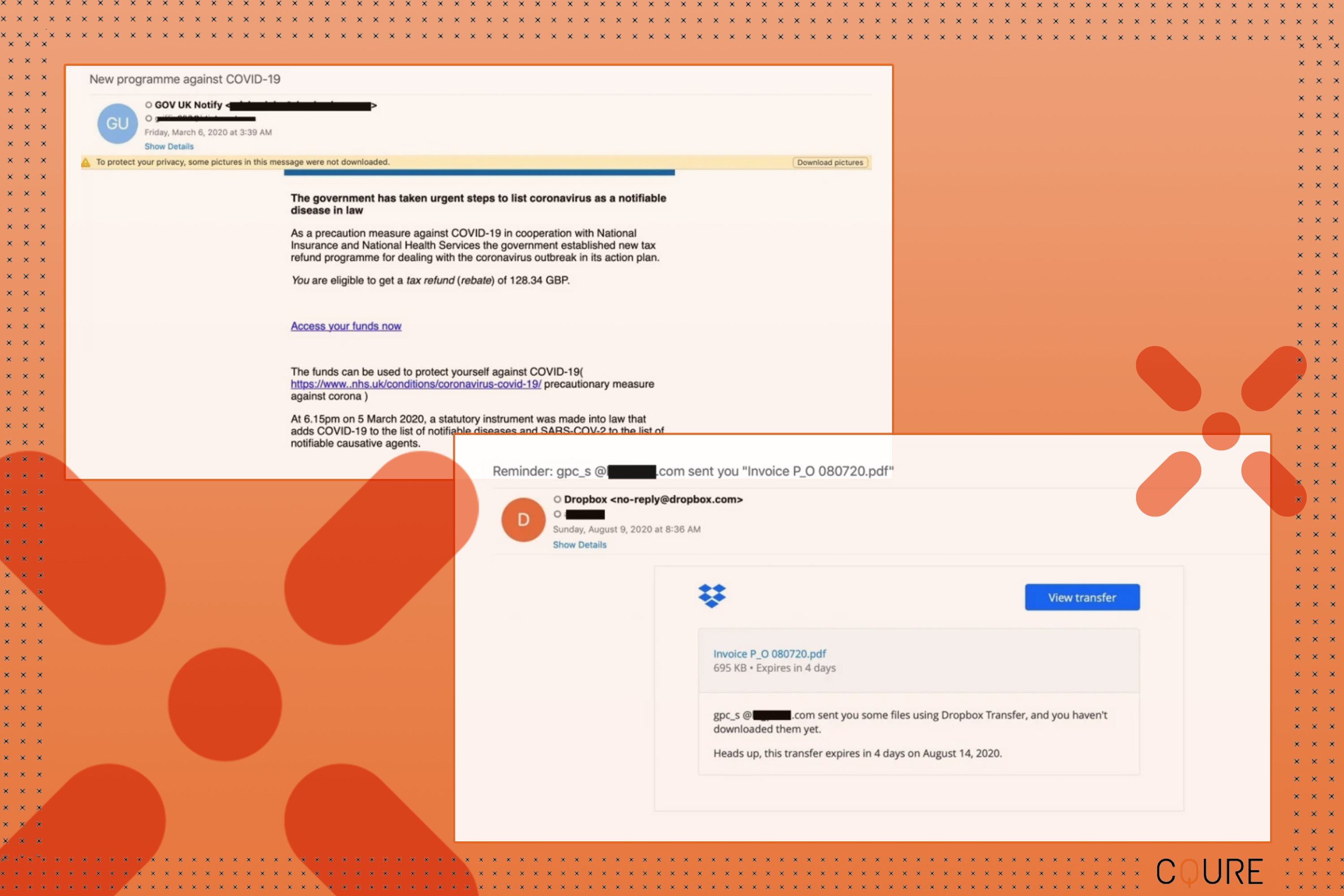
All variants of phishing can be effective, as not all systems have an obvious visual warning that the email, text, or call is not from a trusted source. Here are some examples of real phishing attacks that happened in 2020, which at a glance, looks legitimate:
What is the goal of phishing? To trick you into giving up your sensitive information (such as your credit card number) or to download malicious software onto your computer that will allow the hacker to access your system or data.
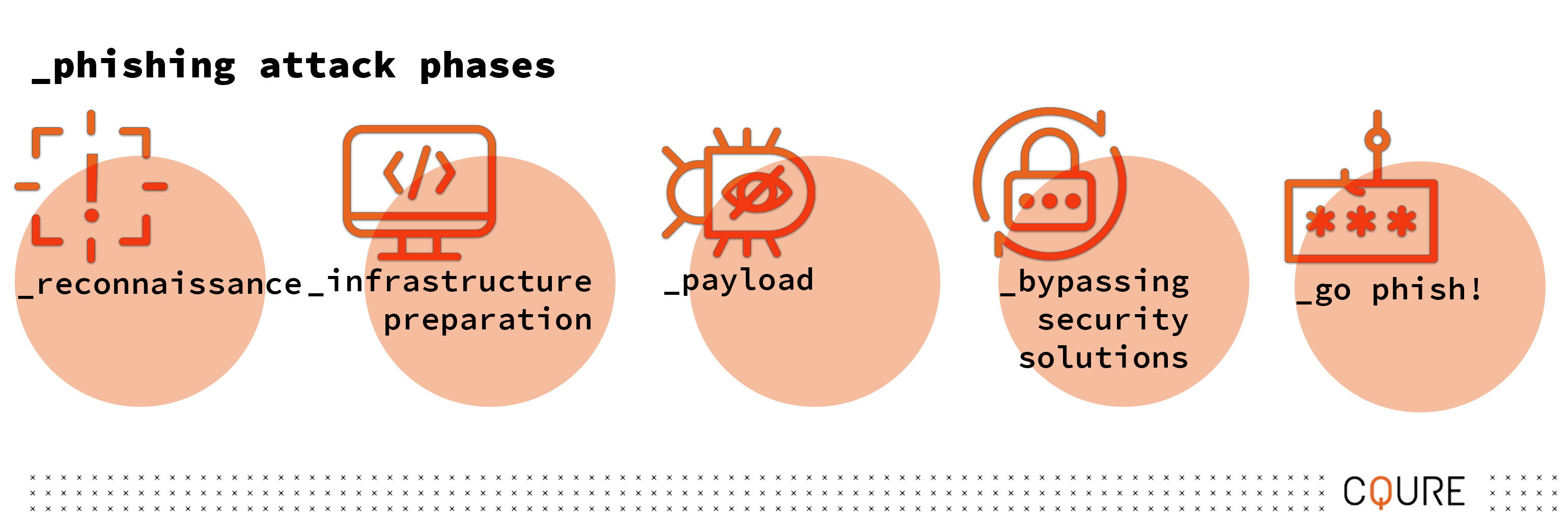
Here’s what actually happens on a hacker’s journey to successfully get access to their target’s computer or other devices.
In this phase, cybercriminals are selecting their victims before the actual attack starts by gathering information. The first step in a targeted attack hacker often uses a methodology called Open Source Intelligence (OSINT). OSINT helps hackers decide who to target by gathering, processing, and disseminating information from publicly available sources.
There is such a wealth of personal information available now thanks to social media and the prevalence of online activities. By using Google hacking, and social media presence, an attacker can easily have almost everything they need to successfully profile an organization or individual.
At the next phase, a cyber attacker will prepare the infrastructure needed for the phishing hook. A phishing hook is the means to collect the private information that the hacker wants to collect from the selected target.
One type of infrastructure that hackers can prepare is mimicking the design of a legitimate website. To make this attack more realistic, an attacker can register a domain similar to the target domain. The attacker can then trick people into thinking that the phishing website is legitimate because of how similar the domain is to the real website.
To prepare this infrastructure, cyberattackers may use tools such as Deepsea and Evilginx2 to act as a landing page or target site. They will then send phishing emails to convince victims to visit the phishing website that they have setup.
Another type of phishing strategy is using a malicious payload. This usually happens in one of two ways (but hackers have rather ingenious minds, and are always trying to find new possibilities to access your computer).
A watering hole attack is an attack where the attacker infects a website (that is visited by the victim) with a malicious payload. The second type, spear-phishing, is an attack where the attacker sends a specially crafted email to the victim, with a malicious payload. Another popular form of spear-phishing is tricking the victim to visit a fake website and download a file with a malicious payload.
These payloads are dormant until they are triggered. Think of it like a mousetrap. The attack (i.e. payload) that harms the victim can only occur if the user has taken an action that triggers the mousetrap to snap.
To successfully prepare efficient payload, hackers use the magic of LOLBINS. An extensive and sophisticated cyberattack will use LOLBINS to plan an attack that is difficult to track because it uses programs or libraries that already exist in your system to launch a fileless attack.
Phase 4: Bypassing Security Solutions
This is the phase where cyberattackers need to bypass existing filters and security, such as passwords and antivirus softwares.
With everything set up, the cyberattacker is ready to go on a phishing expedition. Victims who fall for the phishing hook will end up: clicking on an executable, multi-stage, or fileless malware that collects credentials internally; or enters their information in a malicious website that can collect payment data and personal information.
A hacker’s final goal is the pay out. Pay out objectives are diverse and can range from selling confidential data on the black market to cashing out credit cards or turning a device into a bot for cryptomining or other attacks.
Education is the first step to protect others from falling victim to social engineering. It goes without say that cybercriminals take advantage of naivety. Therefore, by educating others on social engineering prevention techniques, you can help reduce the number of cyberattacks.
If you know someone who still need this advaice, here are some of the best practices you can share with even non-technical users (and implement yourself) to prevent falling for social engineering tactics such as phishing.

If you want to play a bigger role in the fight against cybercriminals, then the next step is to deepen your knowledge in cybersecurity. The most effective way to level up your cybersecurity skills is with the approach of knowing your enemy.
Learning how cyberattackers think is the most effective strategy to not just prevent cyberattacks, but also to quickly diagnose and remediate any attacks that have occurred. The best way to get inside a hacker’s head is by learning through real-world scenarios to build your cybersecurity skills. By gaining this grassroots experience, you will understand how cyber attackers think and know how to implement security measures that will be effective against them.
The advantage of understanding an attacker’s mindset helps you to not just prevent cyberattacks, but also to anticipate them. Having this skillset as a cybersecurity expert makes you an invaluable asset to any organisation.
According to a 2021 Tessian report by, 75% of organisations around the world experienced some kind of phishing attack. It is crucial to understand a full cost of a phishing attack, as it can be tremendous. The Tessian report goes to reveal that the average cost of a compromised record is $150, while the average cost of a data breach is $3.92M.
With cyber threats creating the potential for large-scale damage, there is a great demand for cybersecurity experts to anticipate and prevent cyberattacks, as well as diagnose and remediate any attacks that have slipped through.
Take a deep dive for a phish. Join the brand-new course from CQURE Academy and learn techniques and methods used to compromise your cybersecurity system.
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.