
Hi Security Passionate! Today is time to play a little bit with offline access combined with the need to solve the problem. How many times did you open the old virtual machine and struggled with the administrative account password? How many times you have been into this situation in the production environment? So get your virtual machine ready–install Windows (whatever version that came after the year 2007), have the ISO image of Windows 7 or 2008 R2 or higher ready, and let’s get ready to ramble! We will use the example of Windows Server 2019:
1. Boot the machine from the Windows Server installation media.
Note: Windows Client can be booted from the Windows Server media as well. On Windows Setup window click Next.
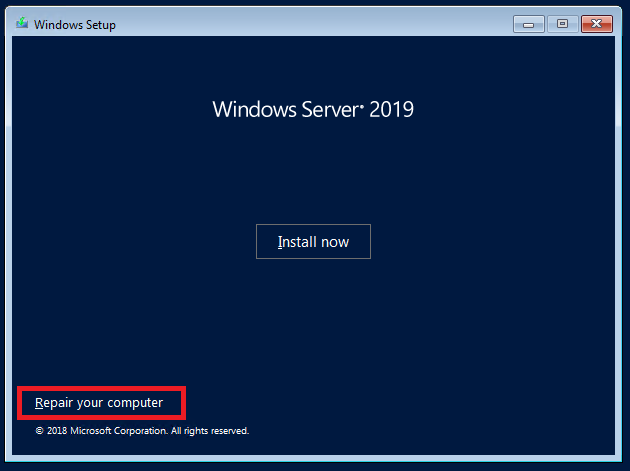
2. Click Repair your computer. DO NOT click Install now.
3. On the Choose an option screen click Troubleshoot:
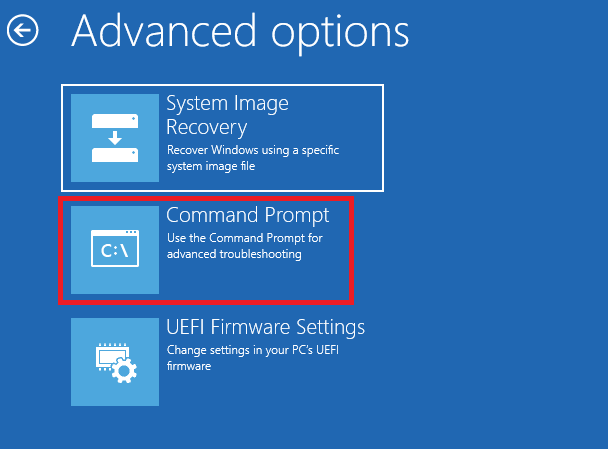
4. On the Advanced options screen pick: Command Prompt. The Command Prompt opens

5. In the Command Prompt type: regedit
a) In the registry editor select HKEY_LOCAL_MACHINE, click File, and then Load Hive…
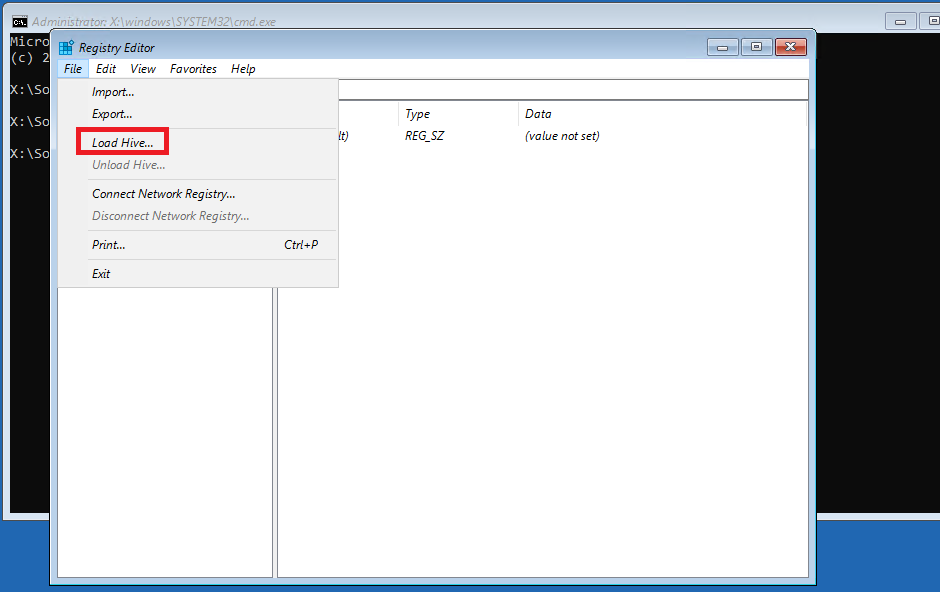
b) In Import Registry File window go to This Computer, pick system drive (default would be C:\)
c) In the Load Hive window, browse to C:\Windows\System32\config\ and Open SOFTWARE registry hive

d) Type some name (it could be e.g. Hackingseries) and click OK
e) In the Registry Editor window expand Hackingseries (which is a SOFTWARE hive loaded) and browse Policies\Microsoft\
f) Right-click on Microsoft and click New > Key

g) Name the new Key: Windows Defender
h) Right-click on newly created Windows Defender key and click New > DWORD (32-bit) Value
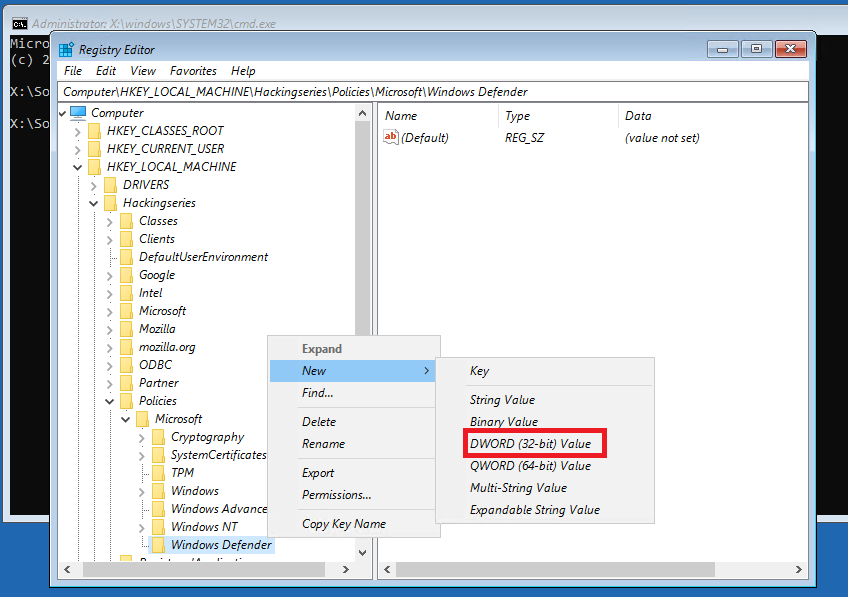
i) Name the new DWORD value: DisableAntiSpyware
j) Right-click on DisableAntiSpyware and click Modify. Then set the value to 1. You should set it as displayed below:
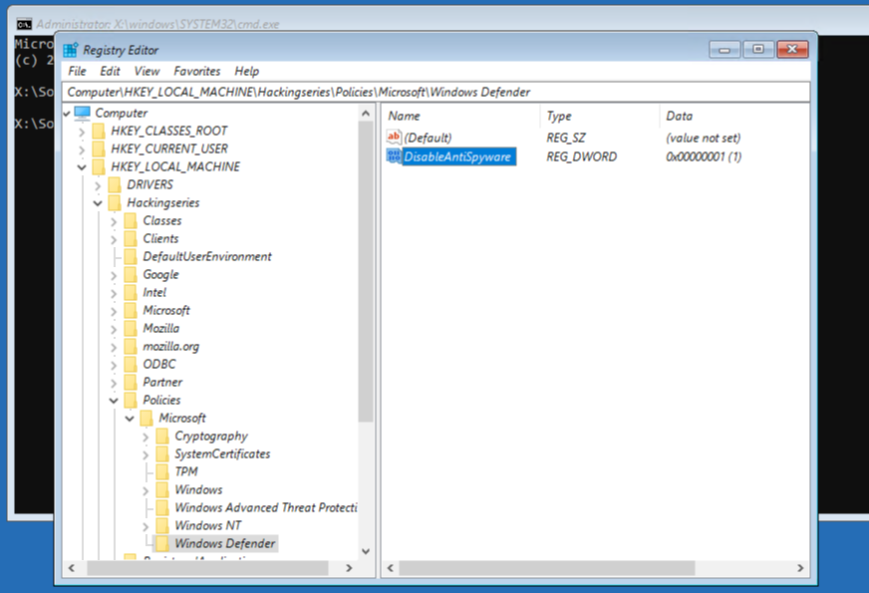
k) You have just disabled Windows Defender to avoid preventing our further actions (without it, the key you will set in a second would be removed). Now go back to Hackingseries and browse to Microsoft\Windows NT\CurrentVersion\Image File Execution Options
l) Right-click on Image File Execution Options and click New > Key. Name the new key: utilman.exe

m) Right-click on newly created key utilman.exe and click New > String Value
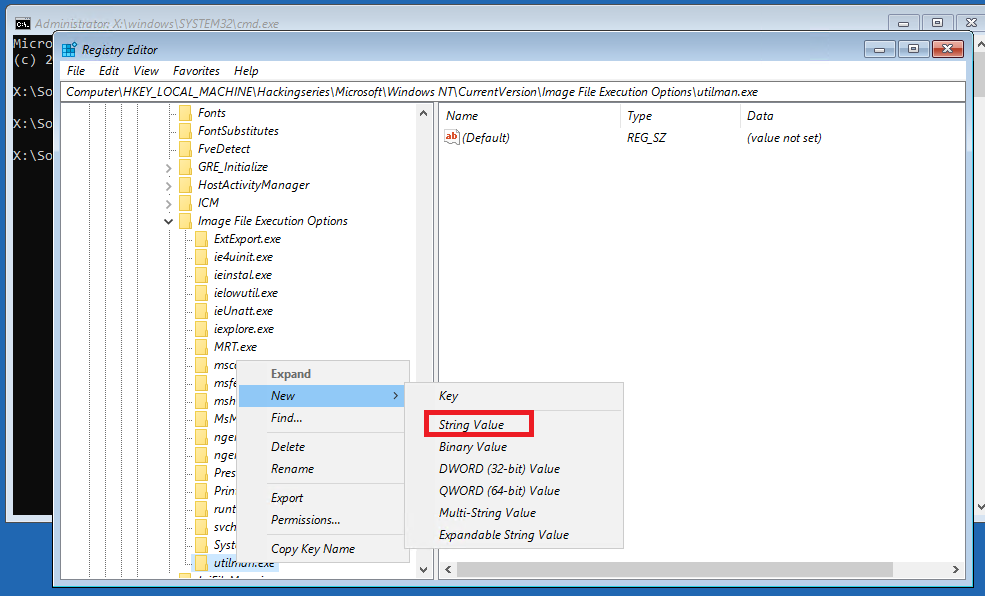
n) Name the new value Debugger and set it to cmd.exe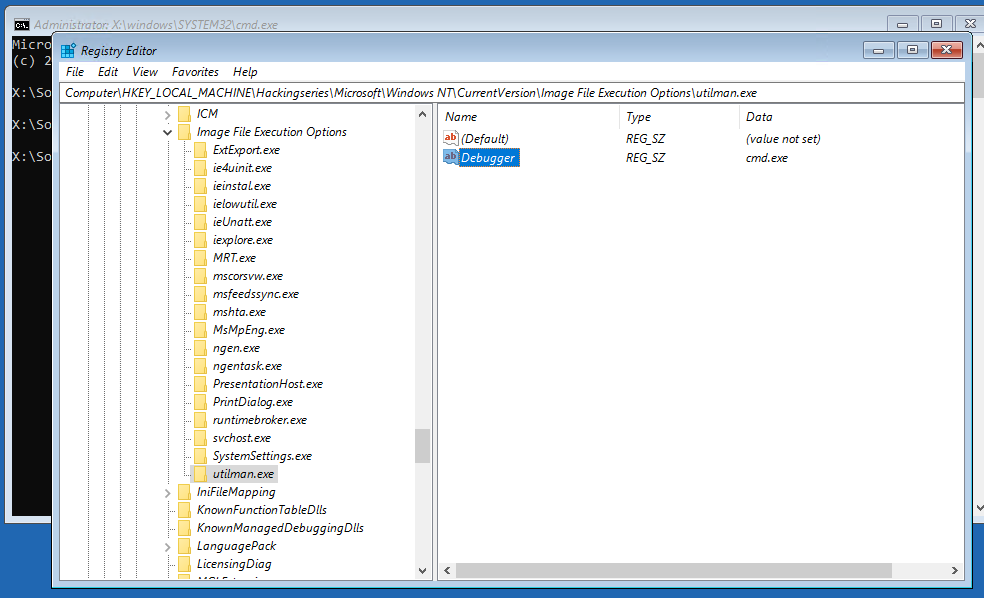
o) Select loaded hive Hackingseries. While selected, click File > Unload Hive…
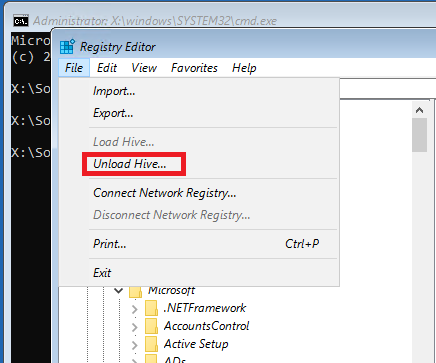
6. Close Registry Editor and Command Prompt. Click Continue on the Choose an option screen. Operating System continues to reboot. This time do not boot from DVD (iso).
7. After the reboot, press the Ease Of Access button in the right bottom corner, the Command Prompt opens. Type the command: whoami. You should be the Local System –the most privileged account in the Operating System, ready to reset your password:
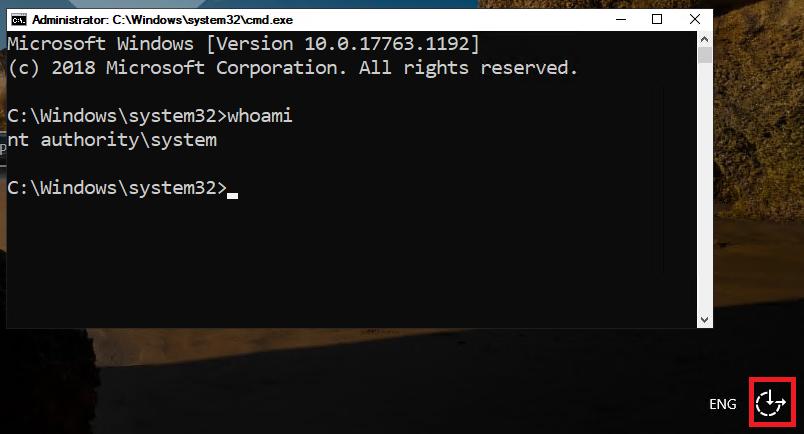
8. Note: Before performing the steps below make sure that you have all encryption-related data (EFS etc.) backed up. This is related to the account tightened Data Protection API, only a user with login credentials that match those of the user who encrypted the data can decrypt the data. However, if something happens, still a user with a roaming profile can decrypt the data from another computer on the network.
9. In the Command Prompt type the following commands:
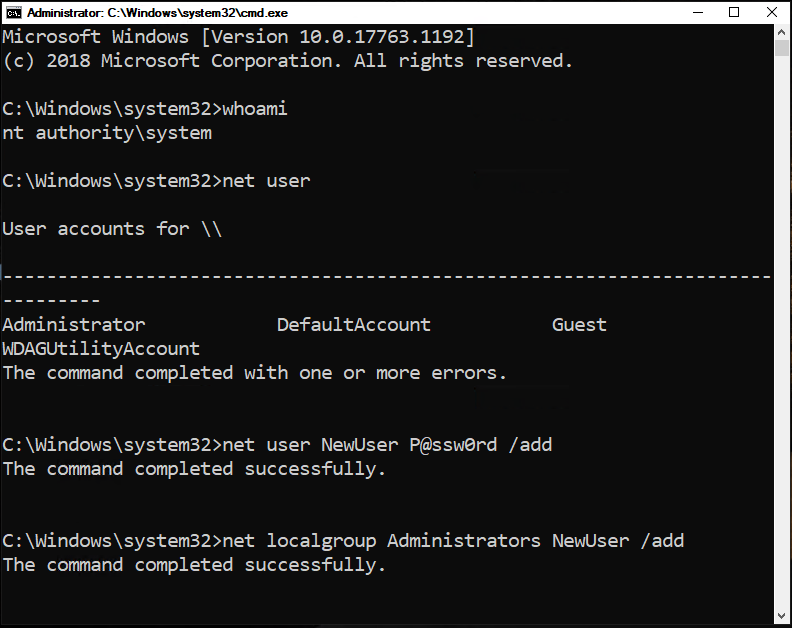
a) To list the existing users: net user
b) If you want to create yourself the new account (recommended): net user NewUser P@ssw0rd /ADD and then add it to the Local Administrators group: net localgroup Administrators NewUser /ADD.
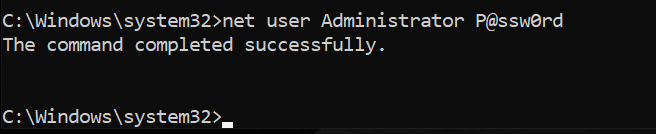
c) To reset the password of the chosen administrative account: net user Administrator P@ssw0rd – remember that /domain switch is needed on the domain controller to process the request at the Domain Controller available and reset the password of the Domain Administrator (net user Administrator P@ssw0rd /domain). If you want to perform these steps on the local workstation (workgroup or domain joined) you do not need to use /domain switch as you work only with the local accounts.
10. After these steps close the Command Prompt and log on with your username and the new password. Enjoy!
Review questions:
Question 1: How to prevent such a possibility?
Question 2: Can a standard user reset the administrator’s password?
In “Episode 2: How to steal the Kerberos tickets” you will read how to steal the identity of the other domain users and who in the enterprise can do it.



Do you want to receive the geekiest cybersecurity solutions, tools, and tricks, straight to your inbox?
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.