
In this article, I will write about a service misconfiguration that I’ve found within the Rockstar Games Launcher (https://socialclub.rockstargames.com/rockstar-games-launcher). The issue is already fixed by the vendor and I was granted a bounty for its discovery and coordinated disclosure.
The interesting trivia about it is that the component was not initially included in the scope of the Rockstar Games program on hackerone. Since then, they have extended the scope to cover the service as well.
Like many other platforms, Rockstar Games Launcher installs additional Windows service, called “Rockstar Service”. Service details can be verified using sc qc <service> command.

The service is used to perform various privileged operations, or as written in the service description, to “ensures the integrity of your Rockstar game library and is used to install, update and uninstall titles.”.
The service’s settings can be also observed in the Windows registry:

What’s important here, is that the quotes around ImagePath value are missing. So… what’s the deal with that?
The Unquoted Service Path is a popular service misconfiguration. Using quotation marks tells Windows to look at the literal path provided in the setting. Without the quotation marks, Windows will attempt to find the binary it is looking for in every folder along the path, and not just at the literal file path provided in the ImagePath setting.
In this case, before executing service installed as “C:\Program Files\Rockstar Games\Launcher\RockstarService.exe”, Windows will also try to execute the following files:
If an attacker manages to plant executable under any of those locations, the execution will be hijacked and planted executable will be started with SYSTEM level permissions which results in Local Privilege Escalation.
In normal Windows installation, both locations should not be writable by normal users, though those restrictions are very often waved by other installed software. Also, this limitation will be waived if the default installation path is changed during installation.
Lastly, any user can restart the service, thus triggering the issue is possible at any time by any Windows user.
The exploitation is rather straightforward. Plant your binary under one of the mentioned locations and restart the service. Any binary will work, although if you want it to keep working, it has to be a valid service type binary.
Once the application is running, you can see that Command Line used to execute the binary is split and the remaining part is treated as an argument to the program. The process is started with full SYSTEM permissions giving binary named Rockstar.exe the ultimate local privileges.
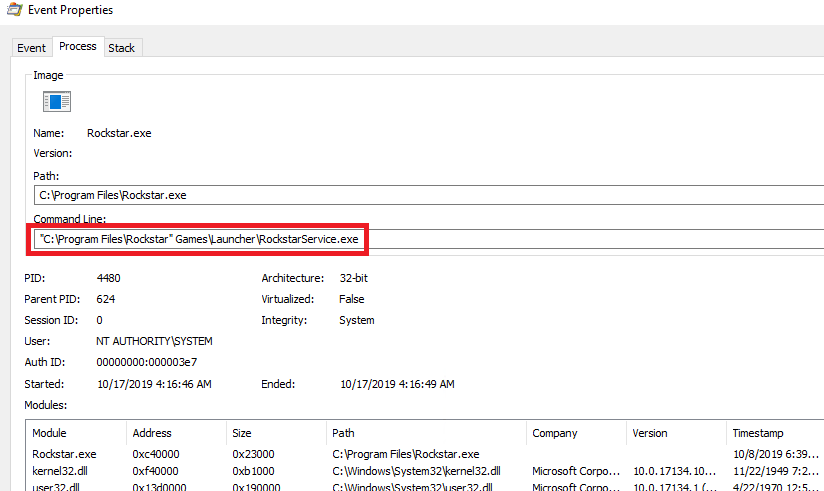
For such situations, we typically employ our CQService tool which enables users to perform privileged actions by writing to a special pipe. Frameworks, such as Metasploit, can also be used to create dedicated service binaries.
Follow me on Twitter @YetAnotherTruth where I share many other interesting findings!
2019-10-17: Discovery
2019-10-17: Reported via Rockstar Games’ Hackerone program (https://hackerone.com/rockstargames)
2019-10-17: First response and confirmation
2019-10-23: Granted bounty $750
2019-11-06: Issue resolved
2019-12-02: Limited disclosure on https://hackerone.com/reports/716448

Adrian Denkiewicz, Cybersecurity Specialist at CQURE, Ethical Hacker, Penetration Tester, Red Teamer, Software Developer, and Trainer. Adrian is deeply interested in the offensive side of security, ranging from modern web attacks, through operating system internals, to low level exploit development. Passionate about learning a bit of everything, but mostly things related to astronomy and rocket science – Adrian has even completed an online rocket science course!



Do you want to receive the geekiest cybersecurity solutions, tools, and tricks, straight to your inbox?
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Learn more about our offer in terms of Consulting. Our Cybersecurity Experts perform consulting work on a daily basis, hence we are fully prepared for any challenge.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.