Back to Basics: Conditional Access in Azure Active Directory

In this beginner’s guide to conditional access in Azure Active Directory, Paula J shows how to regulate access by user, format and device type.

In this beginner’s guide to conditional access in Azure Active Directory, Paula J shows how to regulate access by user, format and device type.

Paula J shows how to use Privileged Identity Management (PIM) in Azure Active Directory security to enforce just-in-time access and manage who has what roles.

Memory dump in general is useful in order to investigate what’s running in our system memory. Everything, all information that was running before the crash is stored in our memory. For example, if there is any kind of malicious code that is running in the memory of a legitimate process, then you would be able […]
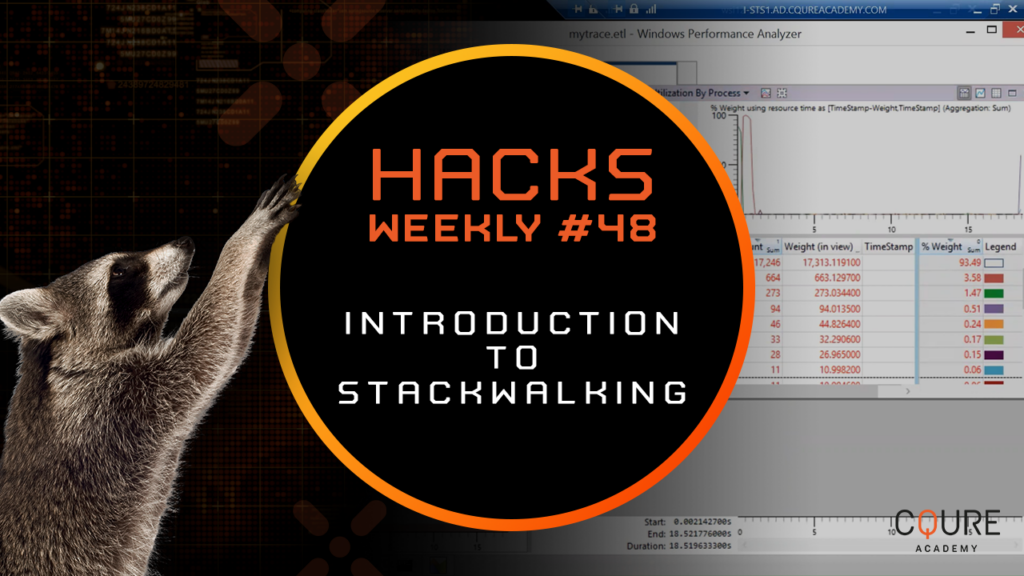
Stackwalking is very useful function which could be enabled in a feature of the Event Tracking for Windows and the Windows Performance Analyzer. ETW is implemented in the Windows operating system. It provides us with a fast and reliable set of event tracing features. When you enable stackwalking for a kernel event, the kernel captures […]
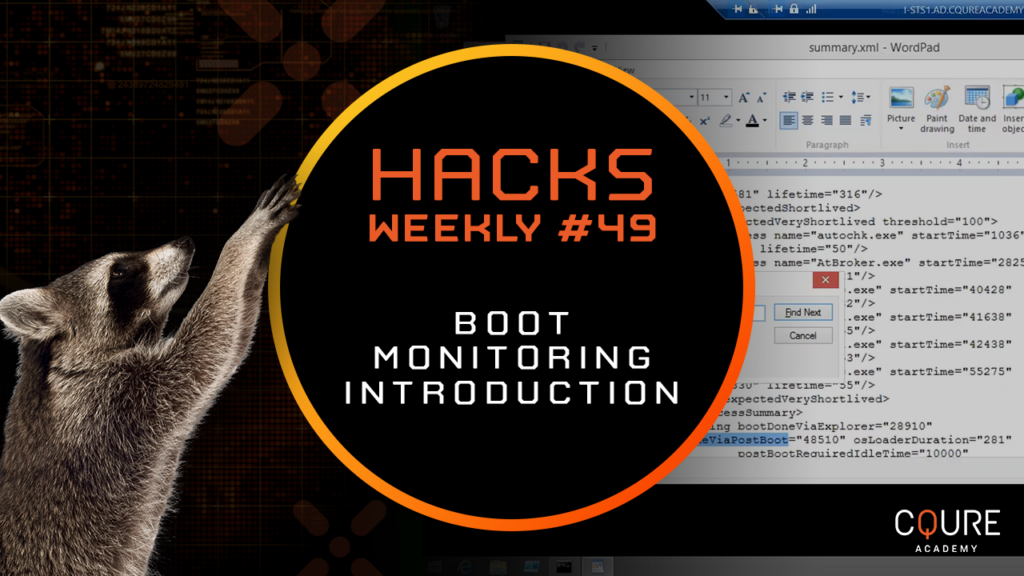
By monitoring the boot process, one might detect a malware infection as some of the malicious executables interfere with Windows system files accessed during the system boot-up resulting in a slower start of it. First of all, please make sure you have set up stack walking. If you have not done it yet, you can […]
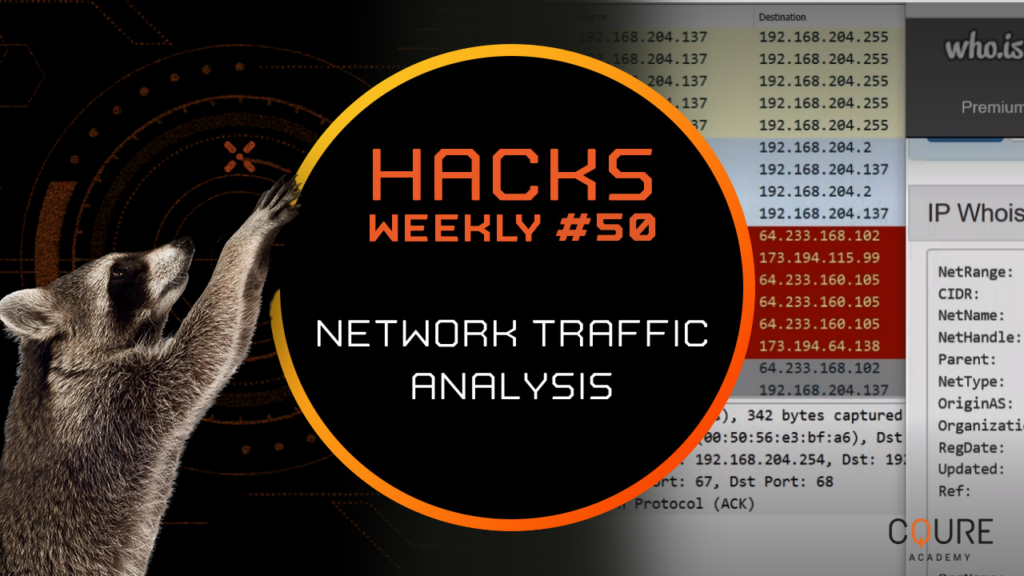
Neutrino, one of the world’s most popular exploit kits, will be the base for our Hacks Weekly scenario. Its malicious code can be injected into legitimate resources – like websites – and compromise a computer through various vendor vulnerabilities. However, due to NTA, we are able to track Neutrino steps and find the root that […]

This time we’re going to talk about Azure AD Identity Protection and investigating risky events related to identities. We’re going to detect, analyze and decide what is happening with our users. First of all, let’s look at the Azure Portal. Let’s launch Portal.azure.com and go to Azure AD Identity Protection where we can see a […]
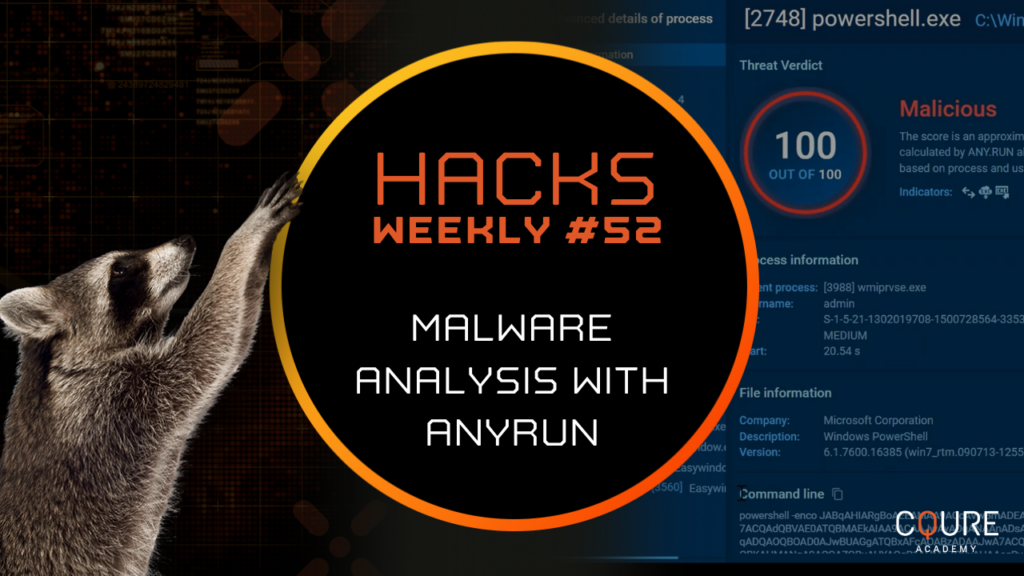
During this scenario, we will work with EMOTET malware. You can watch our video version of this Hacks Weekly episode to see the whole process of infecting the endpoint with this malware. Our first step is searching for all processes that EMOTET malware can execute. In the bottom right corner of the AnyRun software, you […]
During the previous Hacks Weekly episode #52 Malware Analysis with AnyRun we went through analyzing malware inside the AnyRun cloud software. Besides AnyRun, cybersecurity professionals use different software and platforms to verify ransomware or test it. This time we will focus on hybrid-analysis.com, which has similar usage to the AnyRun website. Our video starts with […]

The first step is to install the Dumping Service. In the video attached, we’re doing it by running CreateDumpingService.bat. We need to start the service by running sc start dumpingservice. Afterwards, we can see the start pending. We can check sc query dumpingservice. Now it is running. The next step is to open the PerfView. […]